PassLeader released the NEWEST CompTIA SY0-501 exam dumps recently! Both SY0-501 VCE dumps and SY0-501 PDF dumps are available on PassLeader, either SY0-501 VCE dumps or SY0-501 PDF dumps have the NEWEST SY0-501 exam questions in it, they will help you passing CompTIA SY0-501 exam easily! You can download the valid SY0-501 dumps VCE and PDF from PassLeader here: https://www.passleader.com/sy0-501.html (1218 Q&As Dumps –> 1235 Q&As Dumps –> 1292 Q&As Dumps –> 1318 Q&As Dumps –> 1366 Q&As Dumps –> 1423 Q&As Dumps –> 1472 Q&As Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu
QUESTION 91
A company has three divisions, each with its own networks and services. The company decides to make its secure web portal accessible to all employees utilizing their existing usernames and passwords, The security administrator has elected to use SAML to support authentication. In this scenario, which of the following will occur when users try to authenticate to the portal? (Select TWO.)
A. The portal will function as an identity provider and issue an authentication assertion.
B. The portal will request an authentication ticket from each network that is transitively trusted.
C. The back-end networks will function as an identity provider and issue an authentication assertion.
D. The back-end networks will request authentication tickets from the portal, which will act as the third-party service provider authentication store.
E. The back-end networks will verify the assertion token issued by the portal functioning as the identity provider.
Answer: AB
QUESTION 92
Which of the following would a security specialist be able to determine upon examination of a server’s certificate?
A. CA public key
B. Server private key
C. CSR
D. OID
Answer: D
QUESTION 93
A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an authorized system. While attempting to determine if an unauthorized user is togged into the home network, the user reviews the wireless router, which shows the following table for systems that are currently on the home network.
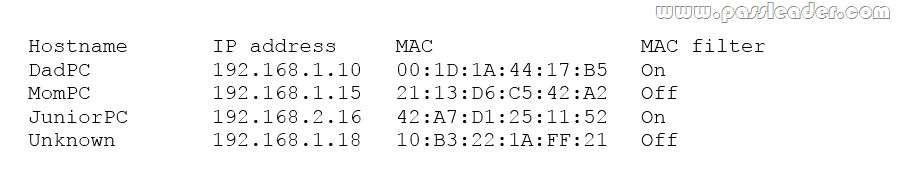
Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
A. Apply MAC filtering and see if the router drops any of the systems.
B. Physically check each of the authorized systems to determine if they are togged onto the network.
C. Deny the “unknown” host because the hostname is not known and MAC filtering is not applied to this host.
D. Conduct a ping sweep of each of the authorized systems and see if an echo response is received.
Answer: C
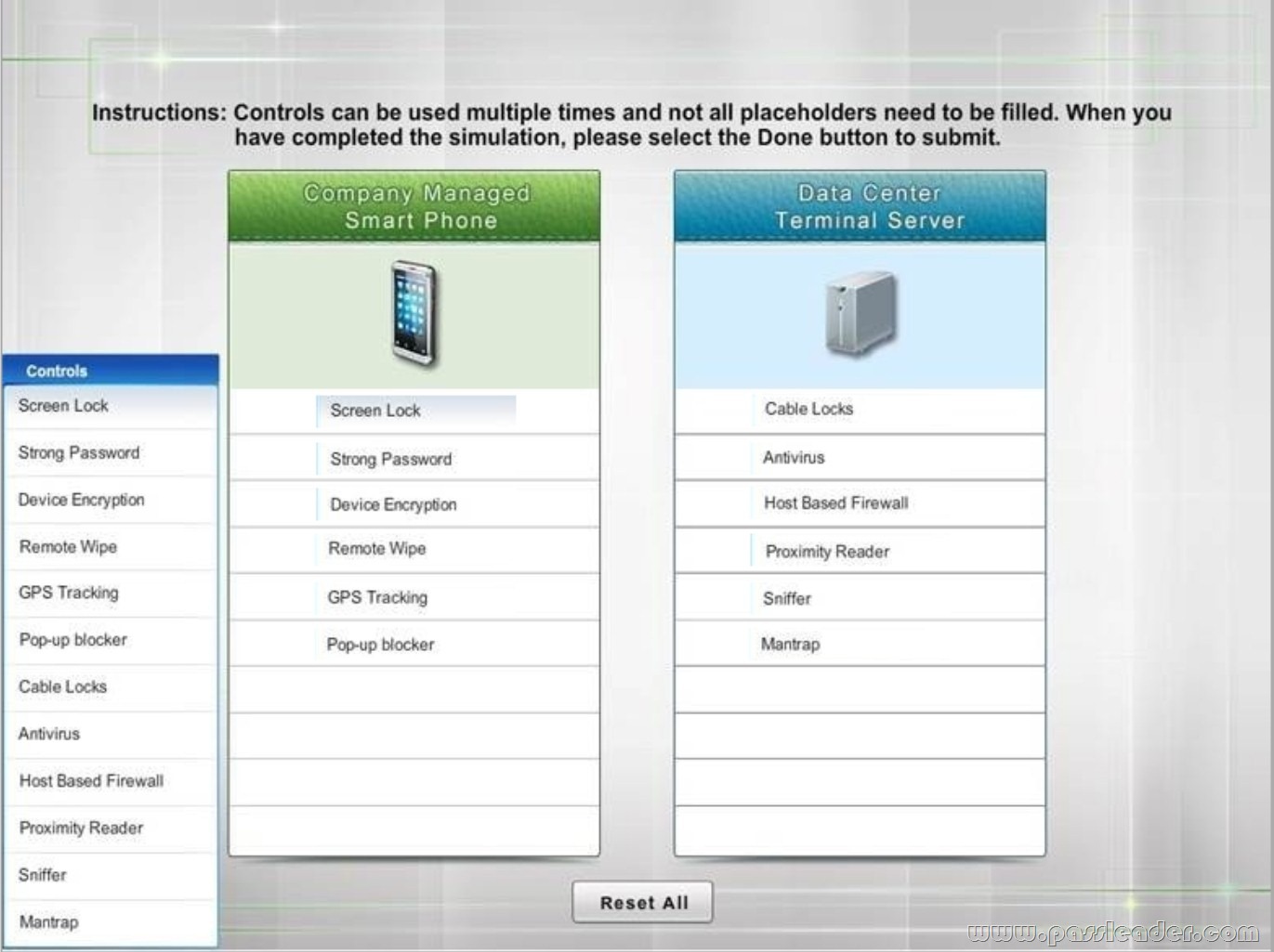
QUESTION 94
Drag and Drop
A Security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and Drop the applicable controls to each asset type.
Instructions: Controls can be used multiple times and not all placeholders needs to be filled. When you have completed the simulation, please select Done button to submit.
QUESTION 95
A security consultant discovers that an organization is using the PCL protocol to print documents, utilizing the default driver and print settings. Which of the following is the MOST likely risk in this situation?
A. An attacker can access and change the printer configuration.
B. SNMP data leaving the printer will not be properly encrypted.
C. An MITM attack can reveal sensitive information.
D. An attacker can easily inject malicious code into the printer firmware.
E. Attackers can use the PCL protocol to bypass the firewall of client computers.
Answer: B
QUESTION 96
A security analyst is hardening a server with the directory services role installed. The analyst must ensure LDAP traffic cannot be monitored or sniffed and maintains compatibility with LDAP clients. Which of the following should the analyst implement to meet these requirements? (Select TWO.)
A. Generate an X.509-complaint certificate that is signed by a trusted CA.
B. Install and configure an SSH tunnel on the LDAP server.
C. Ensure port 389 is open between the clients and the servers using the communication.
D. Ensure port 636 is open between the clients and the servers using the communication.
E. Remove the LDAP directory service role from the server.
Answer: BD
QUESTION 97
Drag and Drop
Drag and drop the correct protocol to its default port.
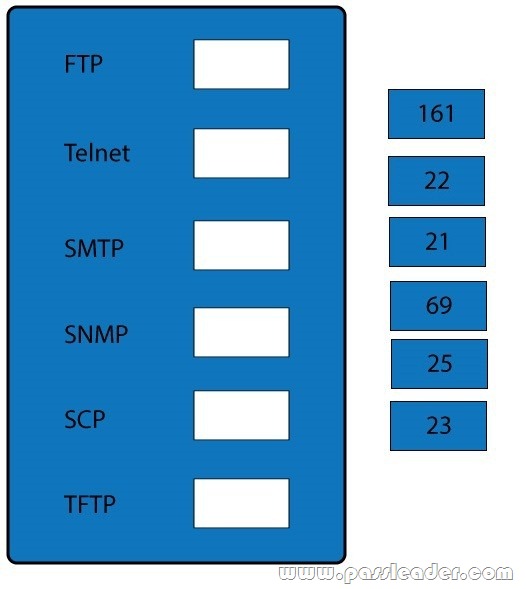
Answer:

Explanation:
– FTP uses TCP port 21.
– Telnet uses port 23.
– SSH uses TCP port 22.
All protocols encrypted by SSH, including SFTP, SHTTP, SCP, SExec, and slogin, also use TCP port 22. Secure Copy Protocol (SCP) is a secure file-transfer facility based on SSH and Remote Copy Protocol (RCP). Secure FTP (SFTP) is a secured alternative to standard File Transfer Protocol (FTP).
– SMTP uses TCP port 25.
– Port 69 is used by TFTP.
– SNMP makes use of UDP ports 161 and 162.
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
QUESTION 98
A botnet has hit a popular website with a massive number of GRE-encapsulated packets to perform a DDoS attack News outlets discover a certain type of refrigerator was exploited and used to send outbound packets to the website that crashed. To which of the following categories does the refrigerator belong?
A. SoC
B. ICS
C. IoT
D. MFD
Answer: C
QUESTION 99
Ann, the Chief Technology Officer (CTO) of a company, is putting together a hardware budget for the next 10 years. She is asking for the average lifespan of each hardware device so that she is able to calculate when she will have to replace each device. Which of the following categories BEST describes what she is looking for?
A. ALE
B. MTTR
C. MTBF
D. MTTF
Answer: D
QUESTION 100
A software developer wants to ensure that the application is verifying that a key is valid before establishing SSL connections with random remote hosts on the Internet. Which of the following should be used in the code? (Select TWO.)
A. Escrowed keys
B. SSL symmetric encryption key
C. Software code private key
D. Remote server public key
E. OCSP
Answer: CE
QUESTION 101
A security guard has informed the Chief Information Security Officer that a person with a tablet has been walking around the building. The guard also noticed strange white markings in different areas of the parking lot. The person is attempting which of the following types of attacks?
A. Jamming
B. War chalking
C. Packet sniffing
D. Near field communication
Answer: B
QUESTION 102
A system administrator is configuring a site-to-site VPN tunnel. Which of the following should be configured on the VPN concentrator during the IKE phase?
A. RIPEMD
B. ECDHE
C. Diffie-Hellman
D. HTTPS
Answer: C
QUESTION 103
A network operations manager has added a second row of server racks in the datacenter. These racks face the opposite direction of the first row of racks. Which of the following is the reason the manager installed the racks this way?
A. To lower energy consumption by sharing power outlets.
B. To create environmental hot and cold isles.
C. To eliminate the potential for electromagnetic interference.
D. To maximize fire suppression capabilities.
Answer: B
QUESTION 104
Phishing emails frequently take advantage of high-profile catastrophes reported in the news. Which of the following principles BEST describes the weakness being exploited?
A. Intimidation
B. Scarcity
C. Authority
D. Social proof
Answer: D
QUESTION 105
Users report the following message appears when browsing to the company’s secure site:
“This website cannot be trusted.”
Which of the following actions should a security analyst take to resolve these messages? (Select TWO.)
A. Verify the certificate has not expired on the server.
B. Ensure the certificate has a .pfx extension on the server.
C. Update the root certificate into the client computer certificate store.
D. Install the updated private key on the web server.
E. Have users clear their browsing history and relaunch the session.
Answer: AC
Welcome to choose PassLeader SY0-501 dumps for 100% passing CompTIA SY0-501 exam: https://www.passleader.com/sy0-501.html (1218 Q&As VCE Dumps and PDF Dumps –> 1235 Q&As VCE Dumps and PDF Dumps –> 1292 Q&As VCE Dumps and PDF Dumps –> 1318 Q&As VCE Dumps and PDF Dumps –> 1366 Q&As VCE Dumps and PDF Dumps –> 1423 Q&As VCE Dumps and PDF Dumps –> 1472 Q&As VCE Dumps and PDF Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu