PassLeader released the NEWEST CompTIA SY0-501 exam dumps recently! Both SY0-501 VCE dumps and SY0-501 PDF dumps are available on PassLeader, either SY0-501 VCE dumps or SY0-501 PDF dumps have the NEWEST SY0-501 exam questions in it, they will help you passing CompTIA SY0-501 exam easily! You can download the valid SY0-501 dumps VCE and PDF from PassLeader here: https://www.passleader.com/sy0-501.html (1292 Q&As Dumps –> 1318 Q&As Dumps –> 1366 Q&As Dumps –> 1423 Q&As Dumps –> 1472 Q&As Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu
NEW QUESTION 1237
When a malicious user is able to retrieve sensitive information from RAM, the programmer has failed to implement ____.
A. session keys
B. encryption of data at rest
C. encryption of data in use
D. ephemeral keys
Answer: C
NEW QUESTION 1238
A commercial cyber-threat intelligence organization observes IoCs across a variety of unrelated customers. Prior to releasing specific threat intelligence to other paid subscribers, the organization is MOST likely obligated by contracts to ____.
A. perform attribution to specific APTs and nation-state actors
B. anonymize any PII that is observed within the IoC data
C. add metadata to track the utilization of threat intelligence reports
D. assist companies with impact assessments based on the observed data
Answer: B
NEW QUESTION 1239
A company that processes sensitive information has implemented a BYOD policy and an MDM solution to secure sensitive data that is processed by corporate and personally owned mobile devices. Which of the following should the company implement to prevent sensitive data from being stored on mobile devices?
A. VDI
B. Storage segmentation
C. Containerization
D. USB OTG
E. Geofencing
Answer: A
NEW QUESTION 1240
A security analyst needs to be proactive in understanding the types of attacks that could potentially target the company’s executives. Which of the following intelligence sources should the security analyst review?
A. Vulnerability feeds.
B. Trusted automated exchange of indicator information.
C. Structured threat information expression.
D. Industry information-sharing and collaboration groups.
Answer: D
NEW QUESTION 1241
An analyst has determined that a server was not patched and an external actor exfiltrated data on port 139. Which of the following sources should the analyst review to BEST ascertain how the incident could have been prevented?
A. The vulnerability scan output.
B. The security logs.
C. The baseline report.
D. The correlation of events.
Answer: B
NEW QUESTION 1242
A recent audit uncovered a key finding regarding the use of a specific encryption standard in a web application that is used to communicate with business customers. Due to the technical limitations of its customers, the company is unable to upgrade the encryption standard. Which of the following types of controls should be used to reduce the risk created by this scenario?
A. Physical
B. Detective
C. Preventive
D. Compensating
Answer: D
NEW QUESTION 1243
A small enterprise decides to implement a warm site to be available for business continuity in case of a disaster. Which of the following BEST meets its requirements?
A. A fully operational site that has all the equipment in place and full data backup tapes on site.
B. A site used for its data backup storage that houses a full-time network administrator.
C. An operational site requiring some equipment to be relocated as well as data transfer to the site.
D. A site staffed with personnel requiring both equipment and data to be relocated there in case of disaster.
Answer: C
NEW QUESTION 1244
A cybersecurity analyst needs to implement secure authentication to third-party websites without users’ passwords. Which of the following would be the BEST way to achieve this objective?
A. OAuth
B. SSO
C. SAML
D. PAP
Answer: C
NEW QUESTION 1245
A security engineer at a manufacturing company is implementing a third-party cloud application. Rather than creating users manually in the application, the engineer decides to use the SAML protocol. Which of the following is being used for this implementation?
A. The manufacturing company is the service provider, and the cloud company is the identity provider.
B. The manufacturing company is the authorization provider, and the cloud company is the service provider.
C. The manufacturing company is the identity provider, and the cloud company is the OAuth provider.
D. The manufacturing company is the identity provider, and the cloud company is the service provider.
E. The manufacturing company is the service provider, and the cloud company is the authorization provider.
Answer: A
NEW QUESTION 1246
Which of the following are the BEST selection criteria to use when assessing hard drive suitability for time-sensitive applications that deal with large amounts of critical information? (Choose two.)
A. MTBF
B. MTTR
C. SLA
D. RTO
E. MTTF
F. RPO
Answer: AB
NEW QUESTION 1247
A security analyst needs to generate a server certificate to be used for 802.1X and secure RDP connections. The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task?
A. Create an OCSP.
B. Generate a CSR.
C. Create a CRL.
D. Generate a .pfx file.
Answer: B
NEW QUESTION 1248
A security consultant was asked to revise the security baselines that are utilized by a large organization. Although the company provides different platforms for its staff, including desktops, laptops, and mobile devices, the applications do not vary by platform. Which of the following should the consultant recommend? (Choose two.)
A. Apply patch management on a daily basis.
B. Allow full functionality for all applications that are accessed remotely.
C. Apply default configurations of all operating systems.
D. Apply application whitelisting.
E. Disable default accounts and/or passwords.
Answer: DE
NEW QUESTION 1249
A security researcher is tracking an adversary by noting its attacks and techniques based on its capabilities, infrastructure, and victims. Which of the following is the researcher MOST likely using?
A. The Diamond Model of Intrusion Analysis.
B. The Cyber Kill Chain.
C. The MITRE CVE database.
D. The incident response process.
Answer: A
NEW QUESTION 1250
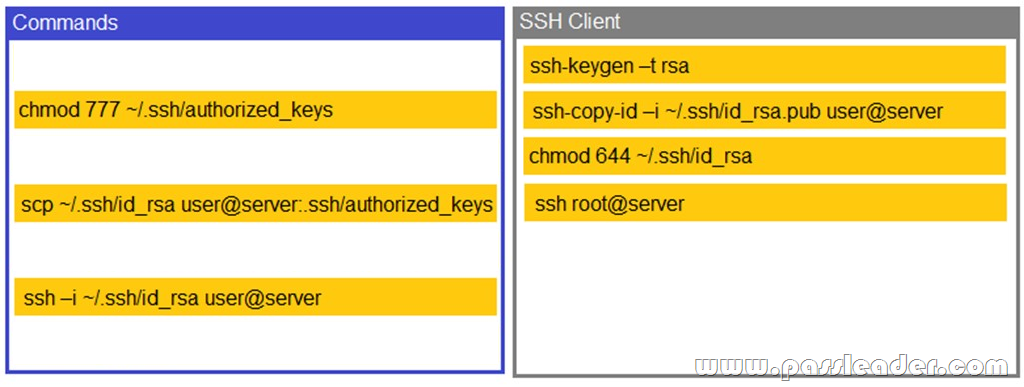
Drag and Drop
A security engineer is setting up passwordless authentication for the first time. Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
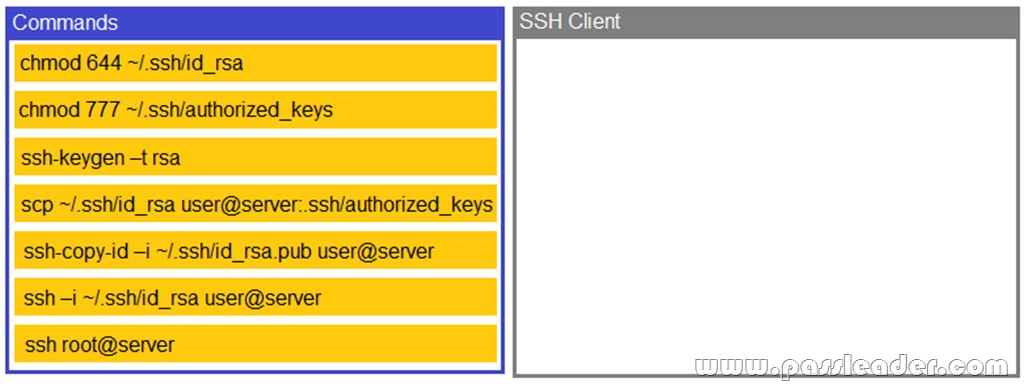
NEW QUESTION 1251
……
Welcome to choose PassLeader SY0-501 dumps for 100% passing CompTIA SY0-501 exam: https://www.passleader.com/sy0-501.html (1292 Q&As VCE Dumps and PDF Dumps –> 1318 Q&As VCE Dumps and PDF Dumps –> 1366 Q&As VCE Dumps and PDF Dumps –> 1423 Q&As VCE Dumps and PDF Dumps –> 1472 Q&As VCE Dumps and PDF Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu