PassLeader released the NEWEST CompTIA CAS-004 exam dumps recently! Both CAS-004 VCE dumps and CAS-004 PDF dumps are available on PassLeader, either CAS-004 VCE dumps or CAS-004 PDF dumps have the NEWEST CAS-004 exam questions in it, they will help you passing CompTIA CAS-004 exam easily! You can download the valid CAS-004 dumps VCE and PDF from PassLeader here: https://www.passleader.com/cas-004.html (572 Q&As Dumps –> 608 Q&As Dumps –> 770 Q&As Dumps ~ Lab Simulations Available)
Also, previewing the NEWEST PassLeader CAS-004 dumps online for free on Google Drive: https://drive.google.com/drive/folders/1xDW57juM57tDgYf7o5sx957VEN2Bv3jc
NEW QUESTION 556
A company recently implemented a CI/CD pipeline and is now concerned with the current state of its software development processes. The company wants to augment its CI/CD pipeline with a solution to:
– Prevent code configuration drifts.
– Ensure coding standards are followed.
Which of the following should the company implement to address these concerns? (Choose two.)
A. Code signing.
B. Fuzzers.
C. Dynamic code analysis.
D. Manual approval processes.
E. Linters.
F. Regression testing.
Answer: EF
NEW QUESTION 557
A SaaS startup is maturing its DevSecOps program and wants to identify weaknesses earlier in the development process in order to reduce the average time to identify serverless application vulnerabilities and the costs associated with remediation. The startup began its early security testing efforts with DAST to cover public-facing application components and recently implemented a bug bounty program. Which of the following will BEST accomplish the company’s objectives?
A. RASP
B. SAST
C. WAF
D. CMS
Answer: B
NEW QUESTION 558
A security manager has written an incident response play book for insider attacks and is ready to begin testing it. Which of the following should the manager conduct to test the playbook?
A. Automated vulnerability scanning.
B. Centralized logging, data analytics, and visualization.
C. Threat hunting.
D. Threat emulation.
Answer: D
NEW QUESTION 559
A company wants to improve the security of its web applications that are running on in-house servers. A risk assessment has been performed, and the following capabilities are desired:
– Terminate SSL connections at a central location.
– Manage both authentication and authorization for incoming and outgoing web service calls.
– Advertise the web service API.
– Implement DLP and anti-malware features.
Which of the following technologies will be the BEST option?
A. WAF.
B. XML gateway.
C. ESB gateway.
D. API gateway.
Answer: D
NEW QUESTION 560
A bank hired a security architect to improve its security measures against the latest threats. The solution must meet the following requirements:
– Recognize and block fake websites.
– Decrypt and scan encrypted traffic on standard and non-standard ports.
– Use multiple engines for detection and prevention.
– Have central reporting.
Which of the following is the BEST solution the security architect can propose?
A. CASB.
B. Web filtering.
C. NGFW.
D. EDR.
Answer: C
NEW QUESTION 561
An organization is running its e-commerce site in the cloud. The capacity is sufficient to meet the organization’s needs throughout most of the year, except during the holidays when the organization plans to introduce a new line of products and expects an increase in traffic The organization is not sure how well its products will be received. To address this issue, the organization needs to ensure that:
– System capacity is optimized.
– Cost is reduced.
Which of the following should be implemented to address these requirements? (Choose two.)
A. Containerization.
B. Load balancer.
C. Microsegmentation.
D. Autoscaling.
E. WAF.
F. CDN.
Answer: BD
NEW QUESTION 562
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices:

Which of the following mobile configuration settings is the mobile administrator verifying?
A. Service set identifier authentication.
B. Wireless network auto joining.
C. 802.1X with mutual authentication.
D. Association MAC address randomization.
Answer: D
NEW QUESTION 563
A company recently deployed a SIEM and began importing logs from a firewall, a file server, a domain controller, a web server, and a laptop. A security analyst receives a series of SIEM alerts and prepares to respond. The following is the alert information:
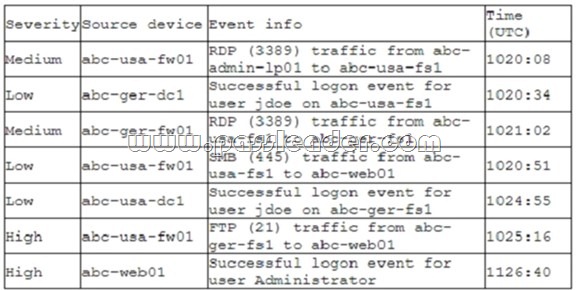
Which of the following should the security analyst do FIRST?
A. Disable Administrator on abc-usa-fs1; the local account is compromised.
B. Shut down the abc-usa-fs1 server; a plaintext credential is being used.
C. Disable the jdoe account; it is likely compromised.
D. Shut down abc-usa-fw01; the remote access VPN vulnerability is exploited.
Answer: C
NEW QUESTION 564
A web service provider has just taken on a very large contract that comes with requirements that are currently not being implemented. In order to meet contractual requirements, the company must achieve the following thresholds:
– 99.99% uptime.
– Load time in 3 seconds.
– Response time = <1.0 seconds.
Starting with the computing environment, which of the following should a security engineer recommend to BEST meet the requirements? (Choose three.)
A. Installing a firewall at corporate headquarters.
B. Deploying a content delivery network.
C. Implementing server clusters.
D. Employing bare-metal loading of applications.
E. Lowering storage input/output.
F. Implementing RAID on the backup servers.
G. Utilizing redundant power for all developer workstations.
H. Ensuring technological diversity on critical servers.
Answer: BCD
NEW QUESTION 565
A security architect is designing a solution for a new customer who requires significant security capabilities in its environment. The customer has provided the architect with the following set of requirements:
– Capable of early detection of advanced persistent threats.
– Must be transparent to users and cause no performance degradation.
– Allow integration with production and development networks seamlessly.
– Enable the security team to hunt and investigate live exploitation techniques.
Which of the following technologies BEST meets the customer’s requirements for security capabilities?
A. Threat intelligence.
B. Deception software.
C. Centralized logging.
D. Sandbox detonation.
Answer: B
NEW QUESTION 566
A global financial firm wants to onboard a new vendor that sells a very specific SaaS application. The application is only hosted in the vendor’s home country, and the firm cannot afford any significant downtime. Which of the following is the GREATEST risk to the firm, assuming the decision is made to work with the new vendor?
A. The application’s performance will be different in regional offices.
B. There are regulatory concerns with using SaaS applications.
C. The SaaS application will only be available to users in one country.
D. There is no geographical redundancy in case of network outages.
Answer: D
NEW QUESTION 567
A company is experiencing a large number of attempted network-based attacks against its online store. To determine the best course of action, a security analyst reviews the following logs:
![]()
Which of the following should the company do NEXT to mitigate the risk of a compromise from these attacks?
A. Restrict HTTP methods.
B. Perform parameterized queries.
C. Implement input sanitization.
D. Validate content types.
Answer: C
NEW QUESTION 568
……
Welcome to choose PassLeader CAS-004 dumps for 100% passing CompTIA CAS-004 exam: https://www.passleader.com/cas-004.html (572 Q&As VCE Dumps and PDF Dumps –> 608 Q&As VCE Dumps and PDF Dumps –> 770 Q&As VCE Dumps and PDF Dumps ~ Lab Simulations Available)
Also, previewing the NEWEST PassLeader CAS-004 dumps online for free on Google Drive: https://drive.google.com/drive/folders/1xDW57juM57tDgYf7o5sx957VEN2Bv3jc