PassLeader released the NEWEST CompTIA SY0-501 exam dumps recently! Both SY0-501 VCE dumps and SY0-501 PDF dumps are available on PassLeader, either SY0-501 VCE dumps or SY0-501 PDF dumps have the NEWEST SY0-501 exam questions in it, they will help you passing CompTIA SY0-501 exam easily! You can download the valid SY0-501 dumps VCE and PDF from PassLeader here: https://www.passleader.com/sy0-501.html (1218 Q&As Dumps –> 1235 Q&As Dumps –> 1292 Q&As Dumps –> 1318 Q&As Dumps –> 1366 Q&As Dumps –> 1423 Q&As Dumps –> 1472 Q&As Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu
QUESTION 106
New magnetic locks were ordered for an entire building. In accordance with company policy, employee safety is the top priority. In case of a fire where electricity is cut, which of the following should be taken into consideration when installing the new locks?
A. Fail safe
B. Fault tolerance
C. Fail secure
D. Redundancy
Answer: A
QUESTION 107
A company hires a consulting firm to crawl its Active Directory network with a non-domain account looking for unpatched systems. Actively taking control of systems is out of scope, as is the creation of new administrator accounts. For which of the following is the company hiring the consulting firm?
A. Vulnerability scanning
B. Penetration testing
C. Application fuzzing
D. User permission
Answer: B
QUESTION 108
Two users need to send each other emails over unsecured channels. The system should support the principle of non-repudiation. Which of the following should be used to sign the users’ certificates?
A. RA
B. CA
C. CRL
D. CSR
Answer: B
QUESTION 109
Multiple employees receive an email with a malicious attachment that begins to encrypt their hard drives and mapped shares on their devices when it is opened. The network and security teams perform the following actions:
– Shut down all network shares.
– Run an email search identifying all employees who received the malicious message.
– Reimage all devices belonging to users who opened the attachment.
Next, the teams want to re-enable the network shares. Which of the following BEST describes this phase of the incident response process?
A. Eradication
B. Containment
C. Recovery
D. Lessons learned
Answer: C
QUESTION 110
Which of the following specifically describes the exploitation of an interactive process to access otherwise restricted areas of the OS?
A. Privilege escalation
B. Pivoting
C. Process affinity
D. Buffer overflow
Answer: A
QUESTION 111
Anne, the Chief Executive Officer (CEO), has reported that she is getting multiple telephone calls from someone claiming to be from the helpdesk. The caller is asking to verify her network authentication credentials because her computer is broadcasting across the network. This is MOST likely which of the following types of attacks?
A. Vishing
B. Impersonation
C. Spim
D. Scareware
Answer: A
QUESTION 112
An administrator discovers the following log entry on a server:
Nov 12 2013 00:23:45 httpd[2342]: GET /app2/prod/proc/process.php?input=change;cd%20../../../etc;cat%20shadow
Which of the following attacks is being attempted?
A. Command injection
B. Password attack
C. Buffer overflow
D. Cross-site scripting
Answer: B
QUESTION 113
A security team wants to establish an Incident Response plan. The team has never experienced an incident. Which of the following would BEST help them establish plans and procedures?
A. Table top exercises
B. Lessons learned
C. Escalation procedures
D. Recovery procedures
Answer: D
QUESTION 114
Which of the following would verify that a threat does exist and security controls can easily be bypassed without actively testing an application?
A. Protocol analyzer
B. Vulnerability scan
C. Penetration test
D. Port scanner
Answer: B
Explanation:
1: A vulnerability scan is the automated process of proactively identifying security vulnerabilities of computing systems in a network in order to determine if and where a system can be exploited and/or threatened. While public servers are important for communication and data transfer over the Internet, they open the door to potential security breaches by threat agents, such as malicious hackers.
2: Vulnerability scanning employs software that seeks out security flaws based on a database of known flaws, testing systems for the occurrence of these flaws and generating a report of the findings that an individual or an enterprise can use to tighten the network’s security.
3: Vulnerability scanning typically refers to the scanning of systems that are connected to the Internet but can also refer to system audits on internal networks that are not connected to the Internet in order to assess the threat of rogue software or malicious employees in an enterprise.
QUESTION 115
Which of the following technologies would be MOST appropriate to utilize when testing a new software patch before a company-wide deployment?
A. Cloud computing
B. Virtualization
C. Redundancy
D. Application control
Answer: B
Explanation:
Virtualization is used to host one or more operating systems in the memory of a single host computer and allows multiple operating systems to run simultaneously on the same hardware, reducing costs. Virtualization offers the flexibility of quickly and easily making backups of entire virtual systems, and quickly recovering the virtual system when errors occur. Furthermore, malicious code compromises of virtual systems rarely affect the host system, which allows for safer testing and experimentation.
QUESTION 116
A system administrator needs to implement 802.1x whereby when a user logs into the network, the authentication server communicates to the network switch and assigns the user to the proper VLAN. Which of the following protocols should be used?
A. RADIUS
B. Kerberos
C. LDAP
D. MSCHAP
Answer: A
QUESTION 117
Which of the following types of cloud Infrastructures would allow several organizations with similar structures and interests to realize shared storage and resources?
A. Private
B. Hybrid
C. Public
D. Community
Answer: D
QUESTION 118
A security administrator has found a hash in the environment known to belong to malware. The administrator then finds this file to be in the preupdate area of the OS, which indicates it was pushed from the central patch system:
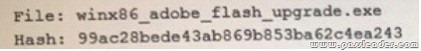
The administrator pulls a report from the patch management system with the following output:

Given the above outputs, which of the following MOST likely happened?
A. The file was corrupted after it left the patch system.
B. The file was infected when the patch manager downloaded it.
C. The file was not approved in the application whitelist system.
D. The file was embedded with a logic bomb to evade detection.
Answer: D
QUESTION 119
Which of the following implements two-factor authentication?
A. A phone system requiring a PIN to make a call.
B. An ATM requiring a credit card and PIN.
C. A computer requiring username and password.
D. A datacenter mantrap requiring fingerprint and iris scan.
Answer: B
QUESTION 120
A company is terminating an employee for misbehavior. Which of the following steps is MOST important in the process of disengagement from this employee?
A. Obtain a list of passwords used by the employee.
B. Generate a report on outstanding projects the employee handled.
C. Have the employee surrender company identification.
D. Have the employee sign an NDA before departing.
Answer: D
Welcome to choose PassLeader SY0-501 dumps for 100% passing CompTIA SY0-501 exam: https://www.passleader.com/sy0-501.html (1218 Q&As VCE Dumps and PDF Dumps –> 1235 Q&As VCE Dumps and PDF Dumps –> 1292 Q&As VCE Dumps and PDF Dumps –> 1318 Q&As VCE Dumps and PDF Dumps –> 1366 Q&As VCE Dumps and PDF Dumps –> 1423 Q&As VCE Dumps and PDF Dumps –> 1472 Q&As VCE Dumps and PDF Dumps) (Wrong Answers Have Been Corrected!!!)
Also, previewing the NEWEST PassLeader SY0-501 dumps online for free on Google Drive: https://drive.google.com/open?id=1Ei1CtZKTLawI_2jpkecHaVbM_kXPMZAu